汇总CTF常见加密算法的解密脚本
XXtea
具体可以查看这篇博客
C实现:
1 |
|
例题1:eztea
解这种题目的时候要注意轮回次数以及递增变量大小
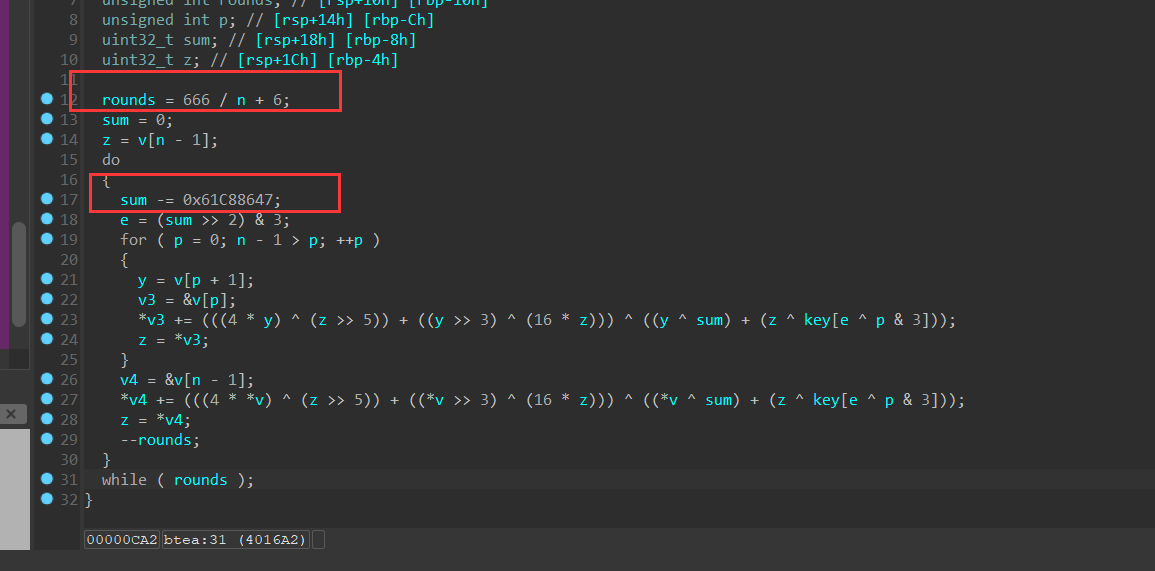
解密脚本:
1 |
|
例题2 2022-DefCampCTF-cup_of_tea
RC4
原理请查看这里
例题1 GUET-CTF2019-encrypt
例题2 2021CISCN-glass
下面给出c实现RC4加密解密代码
1 | #include <stdio.h> |
LCG(线性同余生成器)
我们设置增量为b,乘数为a,模数为n,seed随机产生,Si为产生的随机数项数
s0 = (a * seed + b) % n
s1 = (a * s0 + b) % n
……
原理实现可以查看这篇博客
ezLCG
seed是随机产生的,需要输入四个正确的seed值。四个challenge对应四个不同的类型,正好可以用这题来学习一下,解密代码来自Facker007师傅。
1 | import os |
1、乘数、增量、模数以及第一项已知
当我们知道乘数a,增量b模数n,以及第一项s0的值:
1 | import os |
解密代码:
1 | from Crypto.Util.number import * |
2、增量未知
增量b未知,但是我们指导乘数a,模数n,以及第一项s0和第二项s1的值
1 | def challenge2(): |
1 | s1 = s0 * a + b (mod n) |
所以先把b求出,在将b带入第一种情况的公式中计算
1 | a=60323727461893512389613444053173573556289769830864516385213165273963439419666 |
3、增量和乘数都未知
不知道增量、乘数,但是我们知道模数和生成的三个项
1 | def challenge3(): |
通过推导,我们能够得出m和第一项s0和s1的关系,进而求出乘数a
1 | s_1 = s0 * a + c (mod n) |
解密代码:
1 | n=104461692199190870384162670916383905806504699111028506483787017106937648022643 |
4.增量,乘数和模数均未知
1 | def challenge4(): |
通过以上的条件,我们可以得知
1 | s1 = s0*a + b (mod n) |

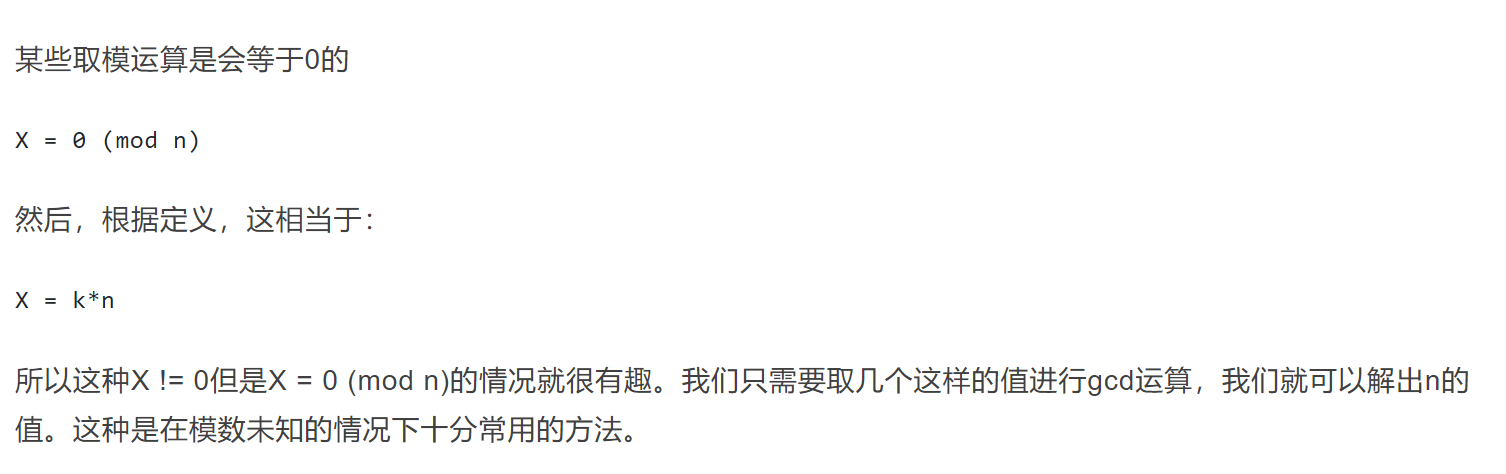
1 | t0 = s1 - s0 |
这样我们就能得知模数的值了,然后和上面的步骤一样,首先是求出乘数a,再求出增量b,最后求出seed
1 | from Crypto.Util.number import * |
RSA
当然也有RSA,详细查看我的另一篇博客
ECC
记录一下XCTF中的一道关于ECC的题目
1 | 已知椭圆曲线加密Ep(a,b)参数为 |
这边使用ECCTOOL来解
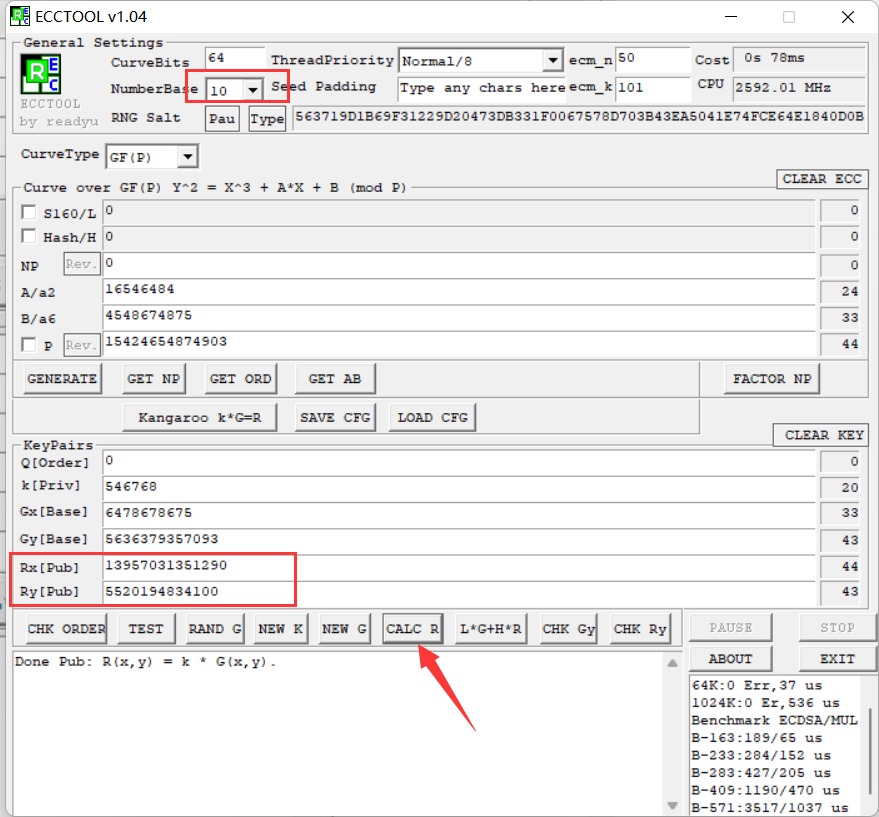
Rx = 13957031351290
Ry = 5520194834100
Rx + Ry = 19477226185390
