这边只记录一些有意思的题,主要是记录复现题
unimod
1 | import random |
我猜测是unnicode编码,找个网站转一下
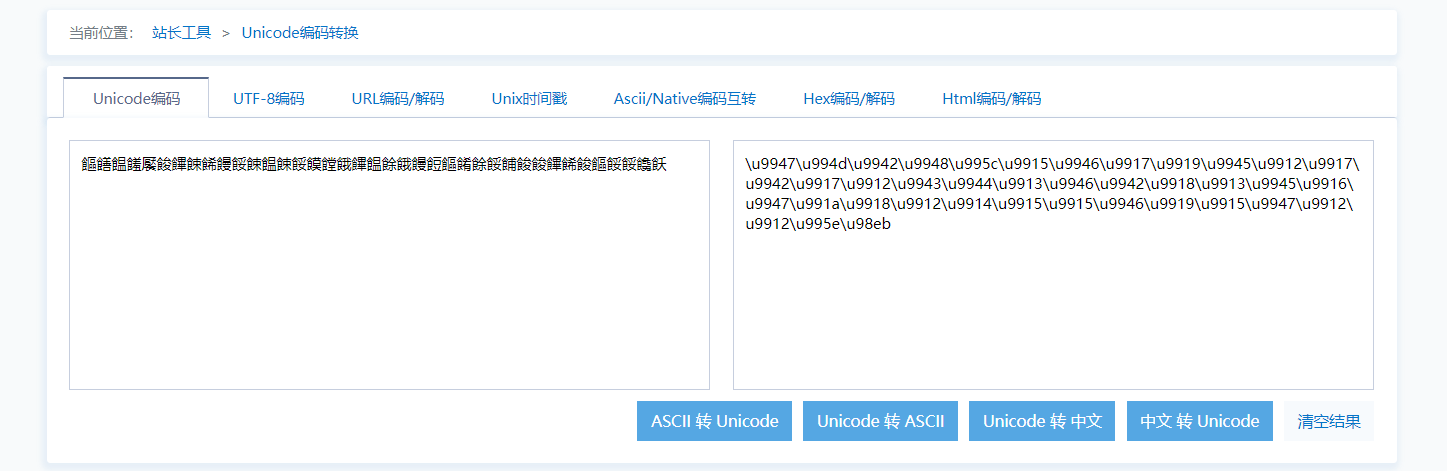
flag第一个字符为”f”,算出k,即可。
1 | ct = [0x9947,0x994d,0x9942,0x9948,0x995c,0x9915,0x9946,0x9917,0x9919,0x9945,0x9912,0x9917,0x9942,0x9917,0x9912,0x9943,0x9944,0x9913,0x9946,0x9942,0x9918,0x9913,0x9945,0x9916,0x9947,0x991a,0x9918,0x9912,0x9914,0x9915,0x9915,0x9946,0x9919,0x9915,0x9947,0x9912,0x9912,0x995e,0x98eb] |
BabyRSAQuiz
这一题还是很有趣的,一共三个挑战,对应三个不同的rsa题型
第一个是最基础的题型
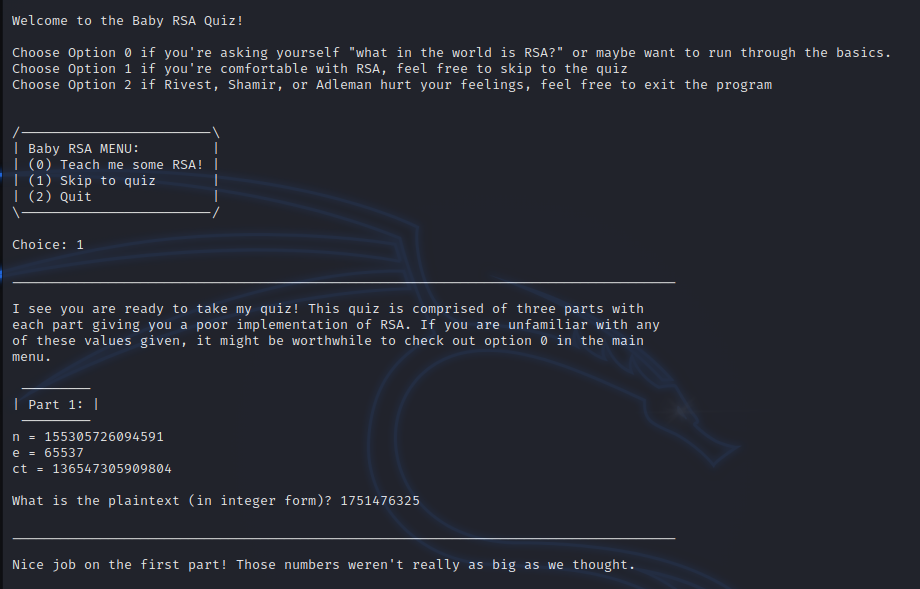
第二个是低加密指数攻击,对n开三次方即可
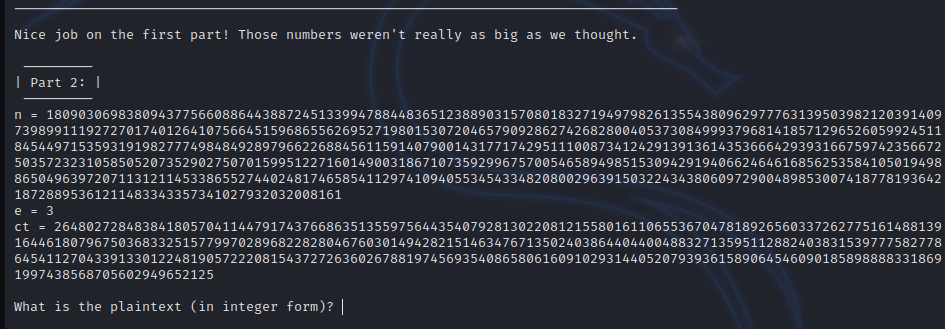
第三个,给出了p和q的大致关系,需要爆破一下,耽搁了挺久的
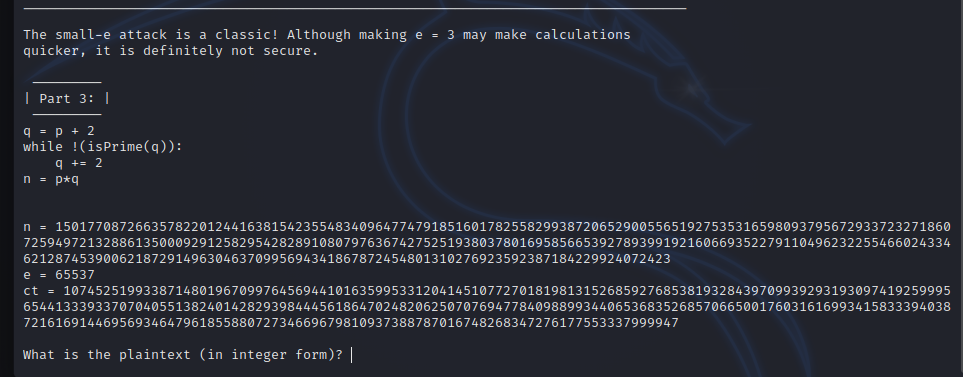
解密脚本
1 | import gmpy2 |
s是n开方之后的结果,通过爆破p和q,获取p*q的值与n的差值,可以确定p = (s-2i),q = (s+2i) ,这样我我们就能确定p和q相对于s的偏移,即可确定p和q的值,进而求解
XORROX
1 | r/bin/env python3 |
这题还是需要去找规律的,不理解意思,硬逆是行不通的
题目首先是随机产生了flag长度的key,然后对每个key[i]与key[0]……key[i-1]元素进行异或,并且将最后异或完成的key[i]值与flag进行异或,所以我们需要求得key列表

1 | xorrox=[1, 209, 108, 239, 4, 55, 34, 174, 79, 117, 8, 222, 123, 99, 184, 202, 95, 255, 175, 138, 150, 28, 183, 6, 168, 43, 205, 105, 92, 250, 28, 80, 31, 201, 46, 20, 50, 56] |
eayrev
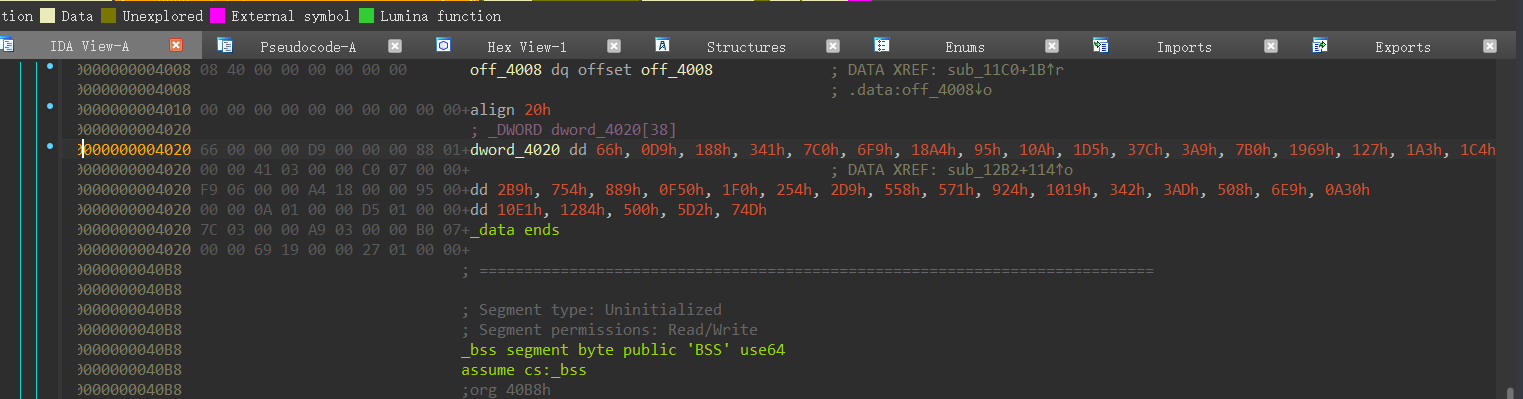
用ida打开,输入用户名之后,输入密码,进入sub_12B2函数
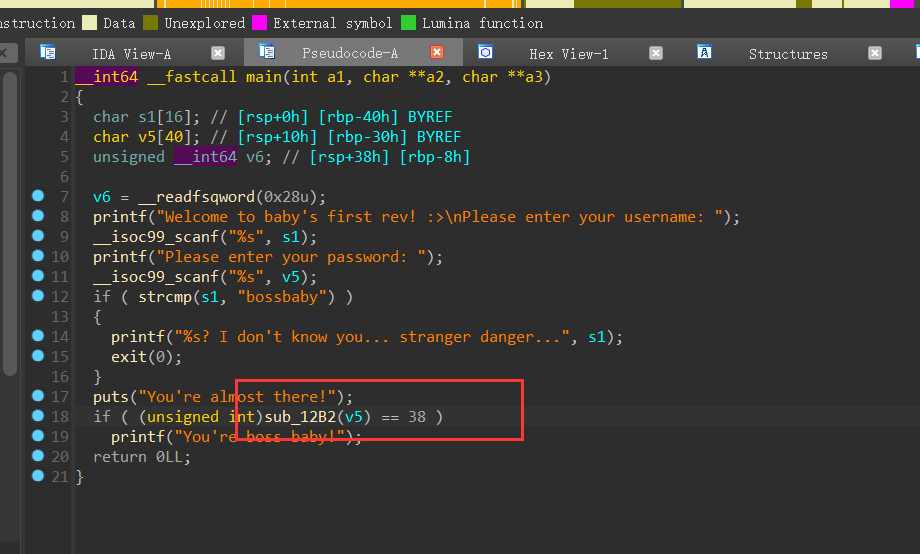
主要加密算法在这边,因为s是char*类型的指针,指向了input传参,v6是input的长度
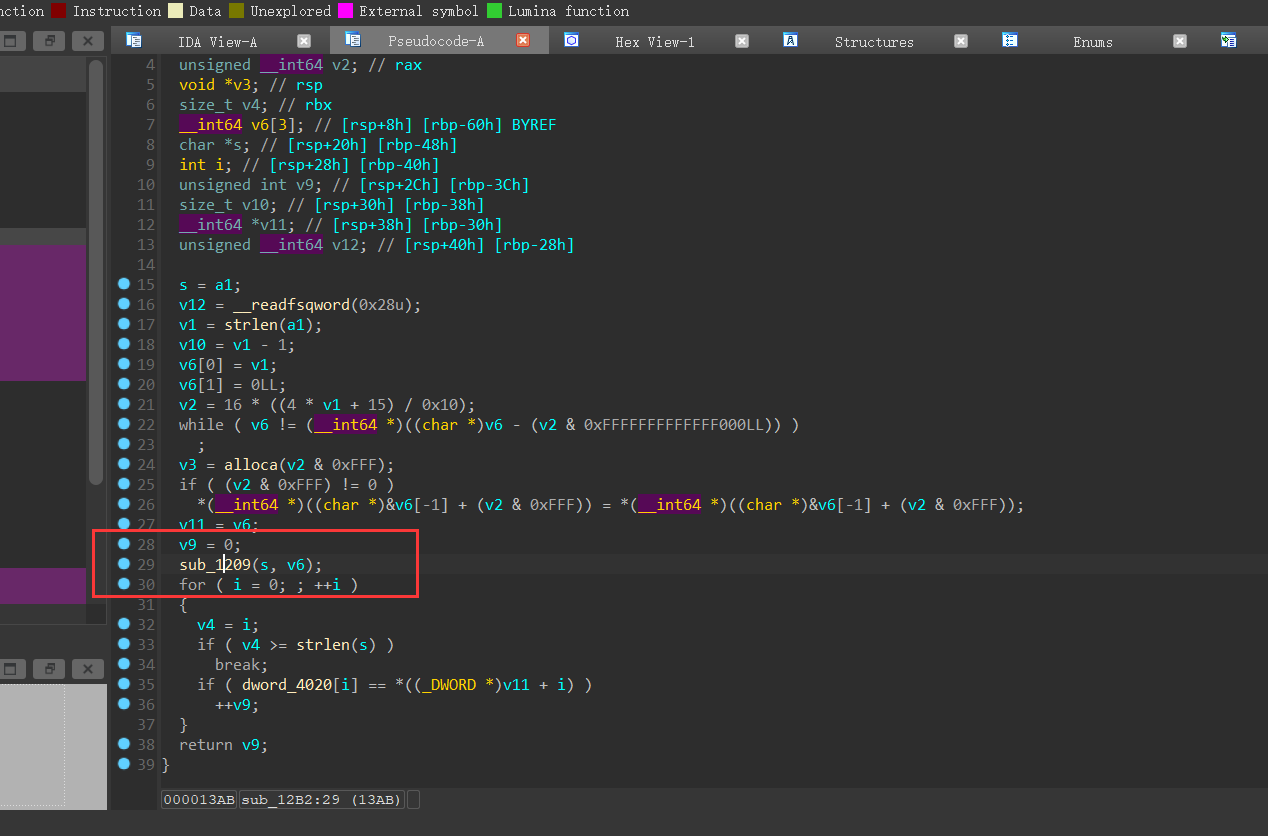
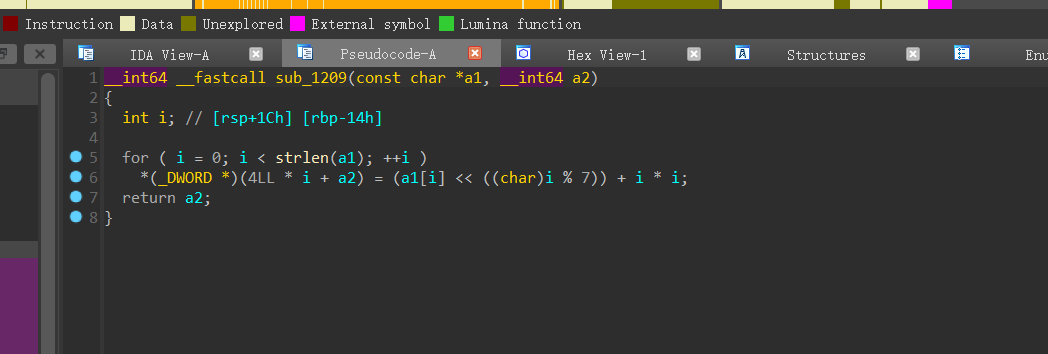
加密结束之后与dword_4020数组进行比较
1 |
|
Quirky
给出的文件:
1 | \x89\x50\x4e\x47\x0d\x0a\x1a\x0a\x00\x00\x00\x0d\x49\x48\x44\x52\x00\x00\x00\x6f\x00\x00\x00\x6f\x01\x03\x00\x00\x00\xd8\x0b\x0c\x23\x00\x00\x00\x06\x50\x4c\x54\x45\x00\x00\x00\xff\xff\xff\xa5\xd9\x9f\xdd\x00\x00\x00\x02\x74\x52\x4e\x53\xff\xff\xc8\xb5\xdf\xc7\x00\x00\x00\x09\x70\x48\x59\x73\x00\x00\x0b\x12\x00\x00\x0b\x12\x01\xd2\xdd\x7e\xfc\x00\x00\x01\x25\x49\x44\x41\x54\x38\x8d\xd5\xd4\x31\x8e\xc3\x20\x10\x05\xd0\xb1\x5c\xd0\x25\x17\x40\x9a\x6b\xd0\x71\x25\xfb\x02\xb6\xf7\x02\xce\x95\xe8\xb8\x06\x92\x2f\x40\x3a\x0a\x94\xd9\x8f\x23\x45\xbb\xc5\x66\x68\x52\x2c\xa2\xe0\x21\x21\xcf\x0c\x83\x49\x7e\x0d\xfa\x1f\xcc\x44\x8b\xaf\x6b\xb0\x44\xac\xf2\x2e\x75\x72\xe3\x66\xea\x2a\x1d\x0c\x76\xc1\xe7\x82\x9d\x4c\x17\x27\x97\xc8\xd4\x4e\xae\x91\xd6\x62\xbb\x28\x75\x8e\xf5\x1a\xed\x2b\xc8\x37\x44\xbe\x73\xb4\x98\xaf\xf4\xdf\xf0\x1c\xf6\x5a\x7e\x16\xf6\x4f\x66\xb2\x64\x78\xf3\xc7\xee\x3a\xe8\x0f\xac\x25\x10\x39\x56\x79\x2f\x74\x71\xe3\x57\x94\x87\x11\x9d\xf1\xd8\x5b\x6c\x34\x79\x9d\x0f\x8f\xb3\xb2\xfb\x73\x53\xa5\x3b\x36\x33\xa2\xf8\x73\x60\x95\x52\xea\x10\xd3\xc5\xf0\x7e\x46\xf5\x9e\x77\x19\x6f\x6d\x4a\x76\x3a\x25\xa0\x49\xda\x05\xdd\x22\xab\x44\xbe\x38\x28\x25\xcd\xa5\x83\x92\x86\x82\x90\x0e\x14\x53\x67\x44\x1f\xd6\x39\xa0\xfe\xac\xb3\x9d\x95\xdd\x10\x19\x51\x89\x91\x3d\x21\xa4\xec\x58\x25\x3a\x76\xf2\x69\x68\xaf\x4c\x54\xe2\x2d\x2c\x1e\x95\xe4\xec\x59\x27\xae\x52\xd0\xb4\x34\x3c\xf3\x55\x89\x85\xf0\xc3\x71\x17\x0b\xdf\x42\x22\x27\x3a\xf1\x7e\xd1\x2d\x68\xaa\xa2\xb3\xe5\xdb\x3a\x56\xb2\xd1\xf9\xb9\x5f\xee\xa7\xf8\x0d\x69\xf5\x37\x77\x6e\xf8\x09\x97\x00\x00\x00\x00\x49\x45\x4e\x44\xae\x42\x60\x82 |
在网上找一个数组转二进制文件的脚本跑一下:
1 | import struct |
之后就会出一个二维码,扫描即可
moblize [复现]
这题记得是没在模拟器上安装成功,就跳过了
赛后复现就尴尬了
OTP Vault (ReactJS逆向)[复现]
使用apktool
1 | apk -d OTPVault.apk |
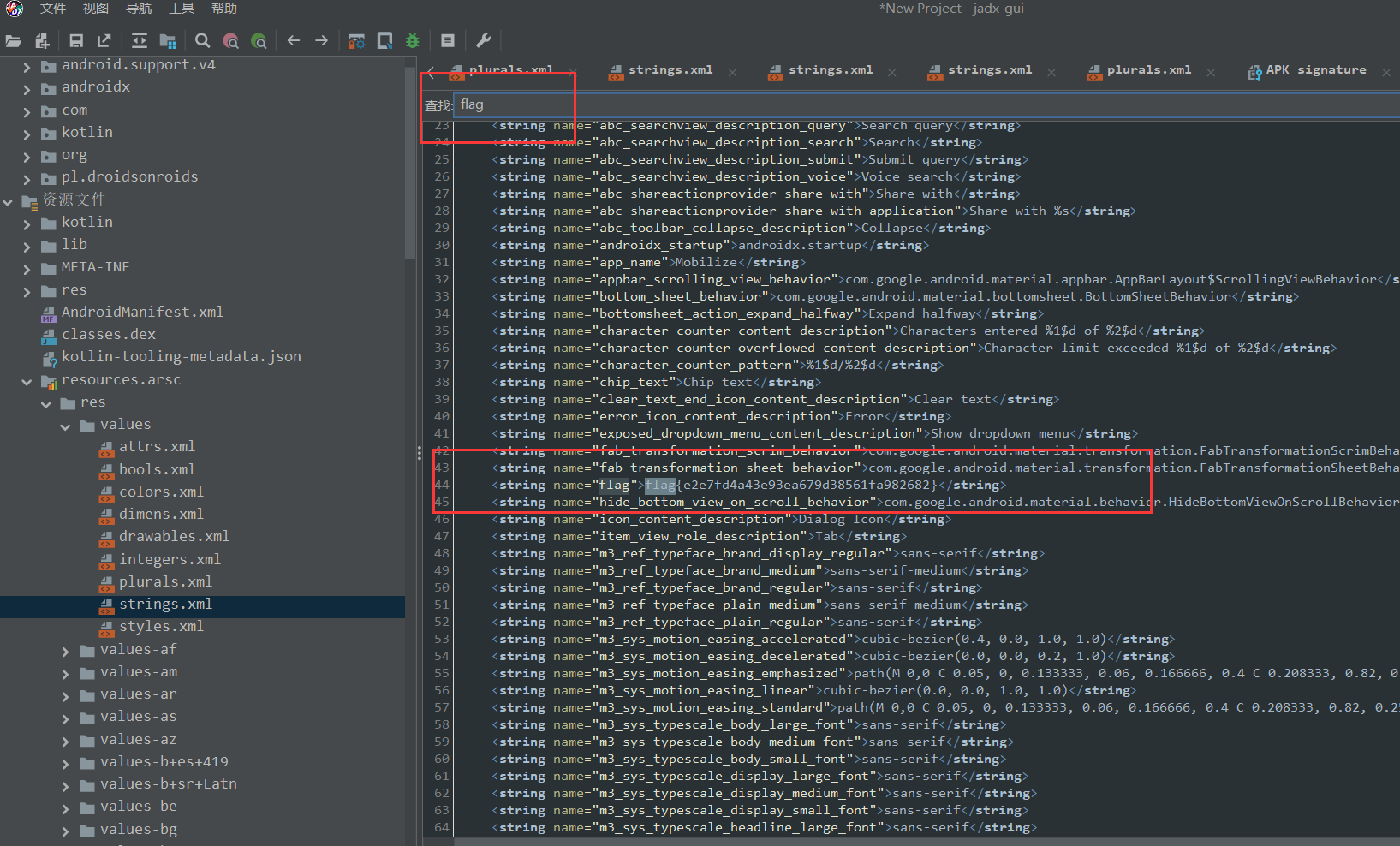
不知道能从jadx反汇编的什么特征,得知该程序是使用ReactJS构建的
wp中使用的是以下的工具来反汇编assets目录下的index.android.bundle,需要node环境
在windows中安装就可以了
1 | npm i -g react-native-decompiler |
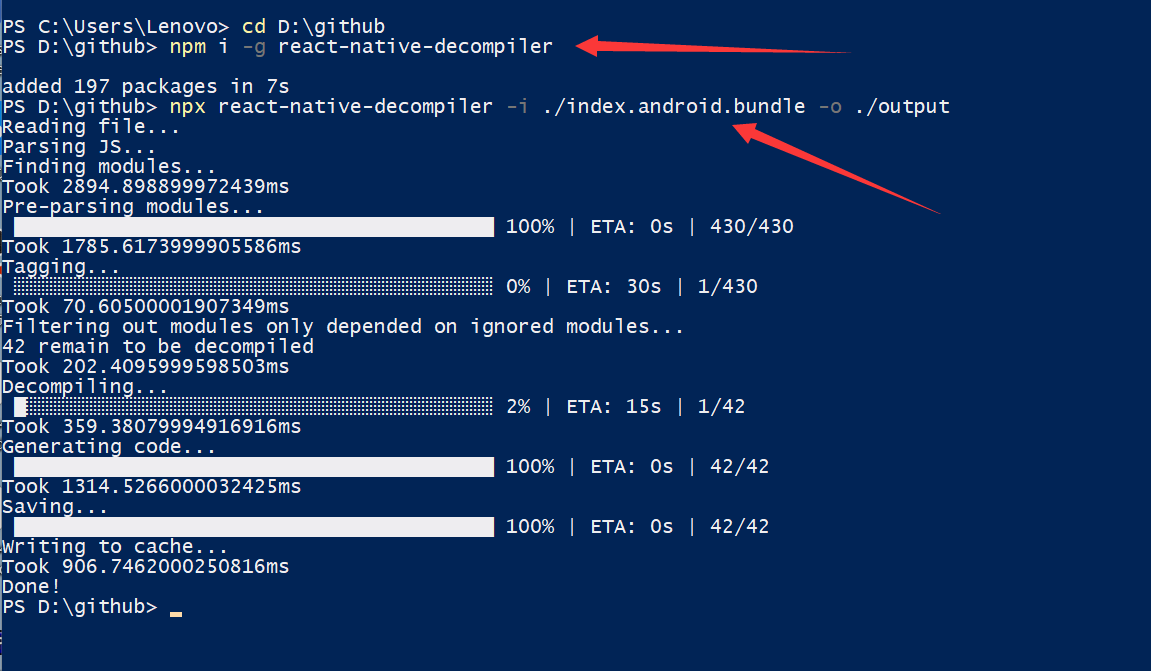
后面发现提取出来的文件有很多的时候,还是转linux了,需要配置一下npm
–更新–
方法原来不止一种,上述方法确实太过麻烦
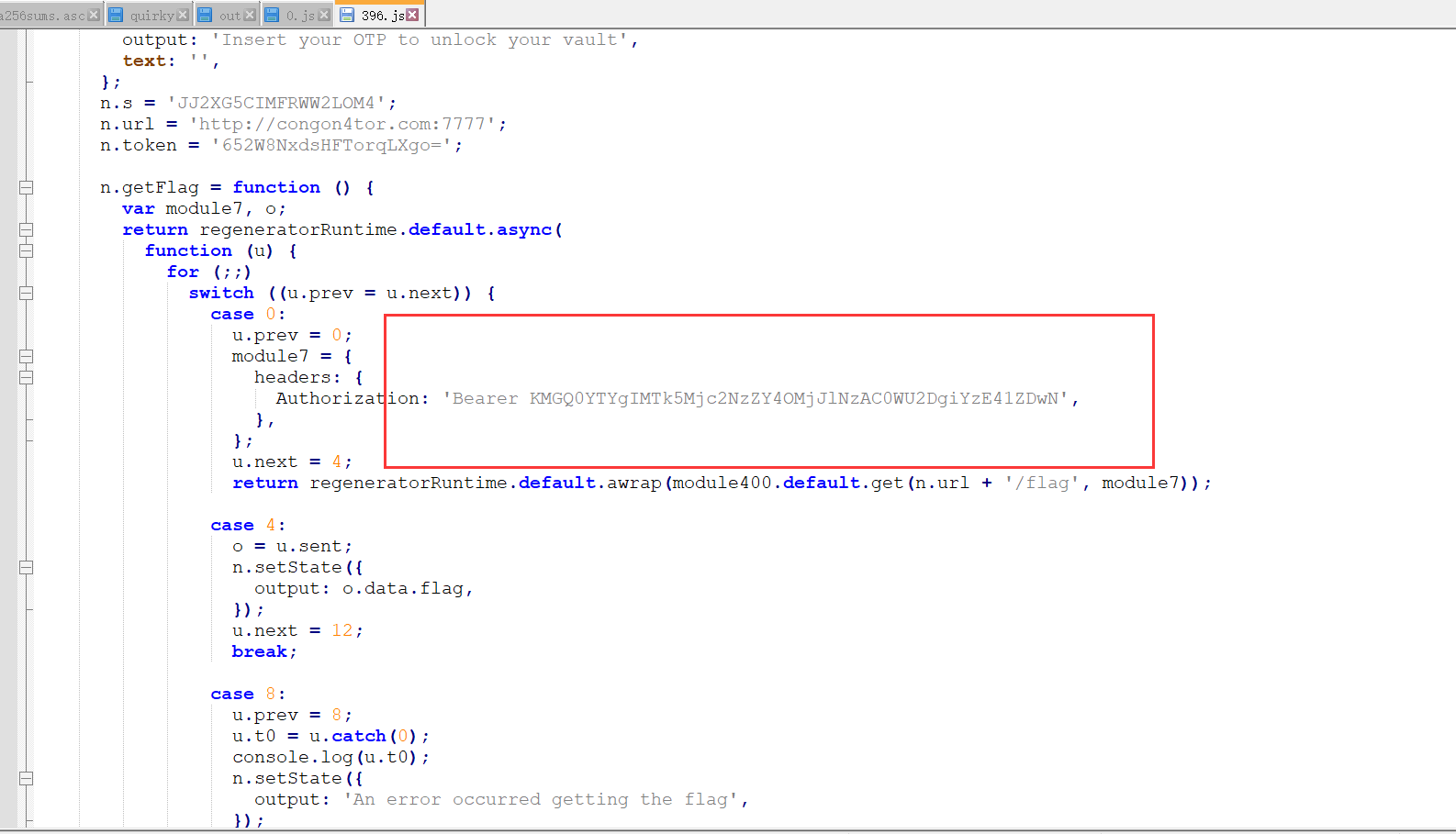
直接把apk后缀改成zip,解压出来,找到assets下面的index.android.bundle,直接用notepad打开,复制代码到VScode中,shift+alt+f,代码格式化,搜索失败字符串”Invalid OTP”。
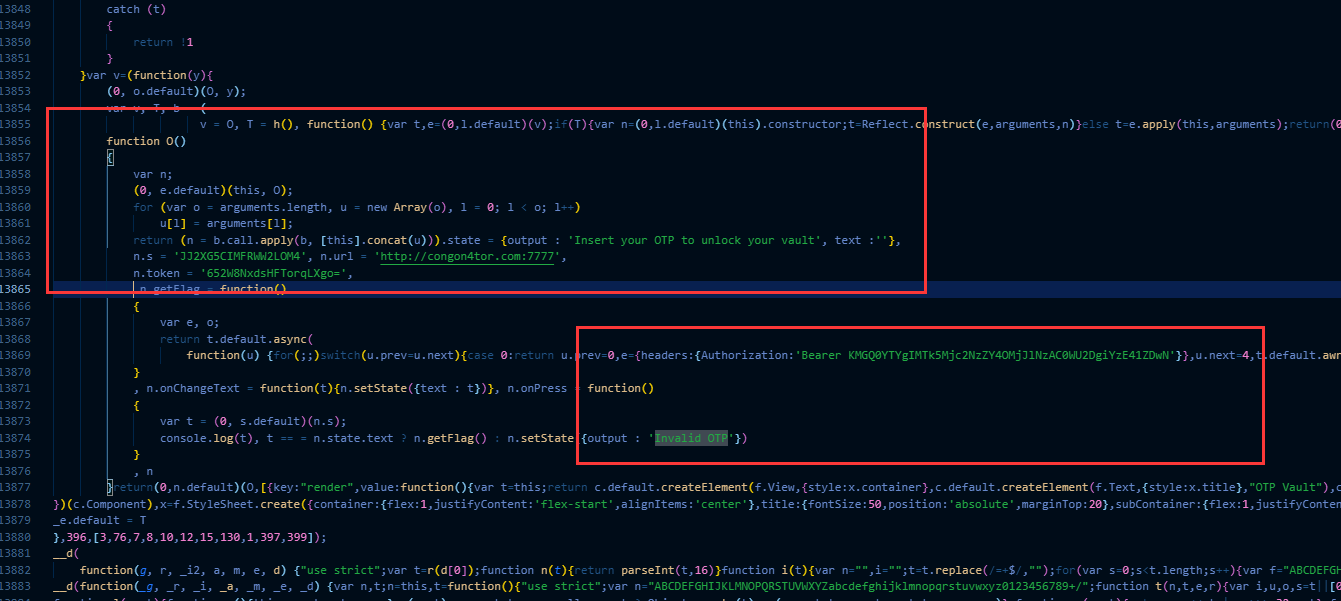
我以为要构造头呢……
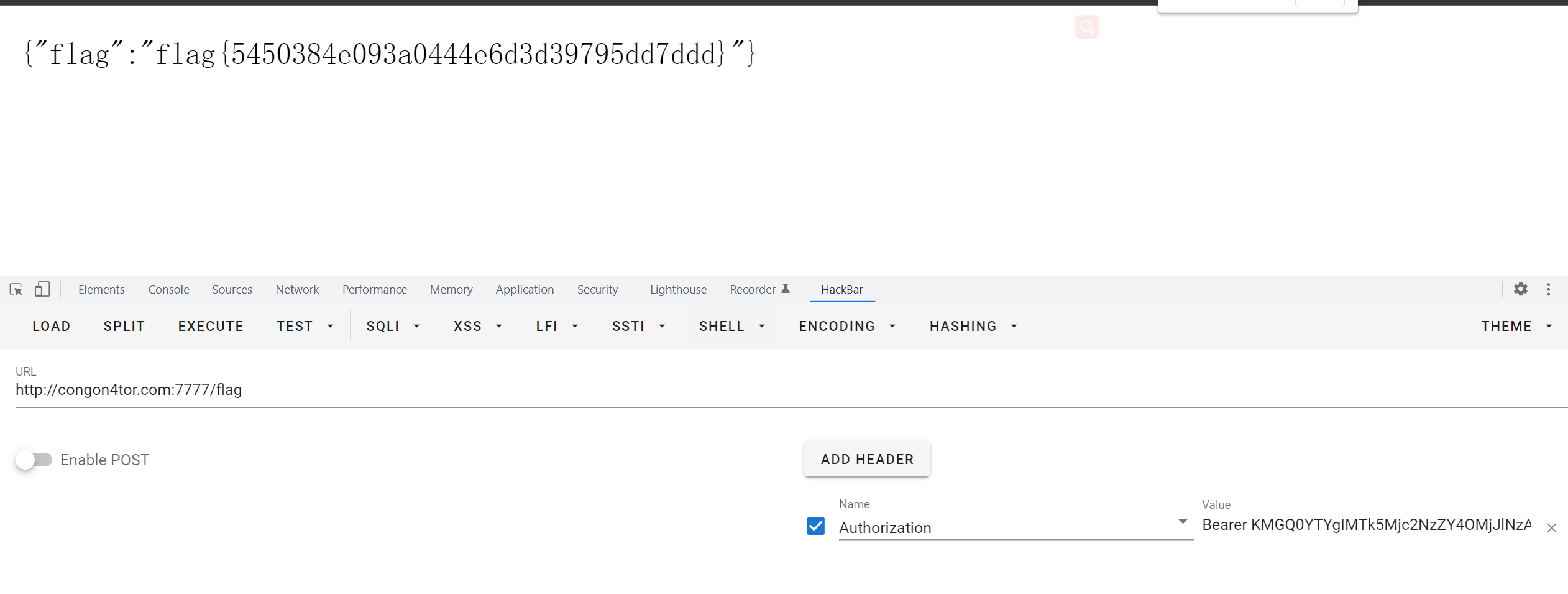
直接上hackbar就行了
flag{5450384e093a0444e6d3d39795dd7ddd}
clickme [复现]
模拟器版本太低,不能安装