复现一下2021CISCN
rsa
题目:
1 | from flag import text,flag |
给出的out文件
1 | 19105765285510667553313898813498220212421177527647187802549913914263968945493144633390670605116251064550364704789358830072133349108808799075021540479815182657667763617178044110939458834654922540704196330451979349353031578518479199454480458137984734402248011464467312753683234543319955893 |
首先是msg1,低加密指数攻击,给c开三次方就可以解出来了,但是谨慎一点,还是使用循环爆破来解比较稳妥。

1 | from gmpy2 import iroot |
然后是msg2,共模攻击
1 | import gmpy2 |
最后一个倒是挺迷惑人的,给出了错误的方向,右移200位,再左移的话,和不告诉我们没有区别……
然后,我找到了这首诗:

不知道msg3的范围,字符串循环爆破即可。
1 | e = 65537 |
python3的生成md5代码:
1 | import hashlib |
python2的生成md5代码:
1 | import md5 |
如果比赛就一个一个的试……
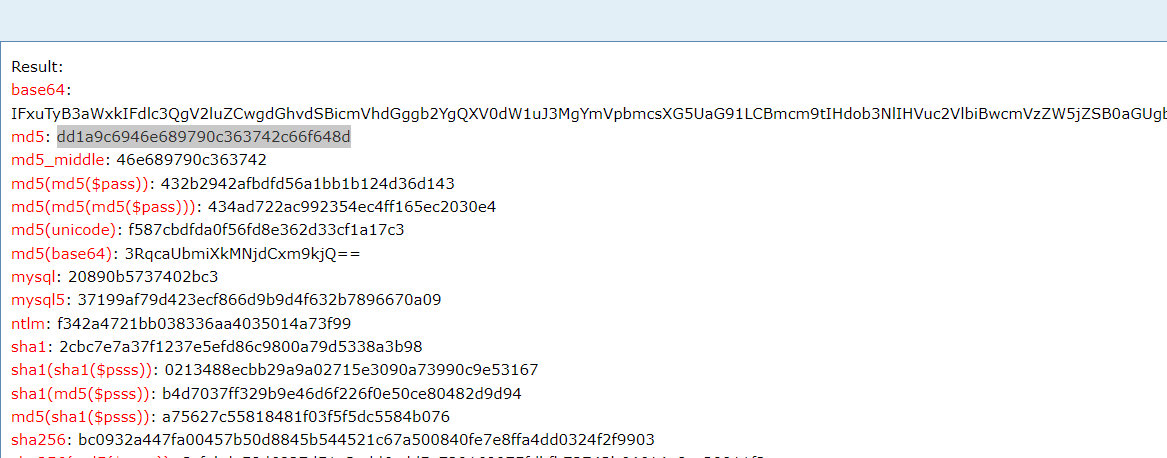
glass
先用jeb查看一下,直接查看没有发现任何加密函数,有点懵,然后发现上面有一个.lib文件
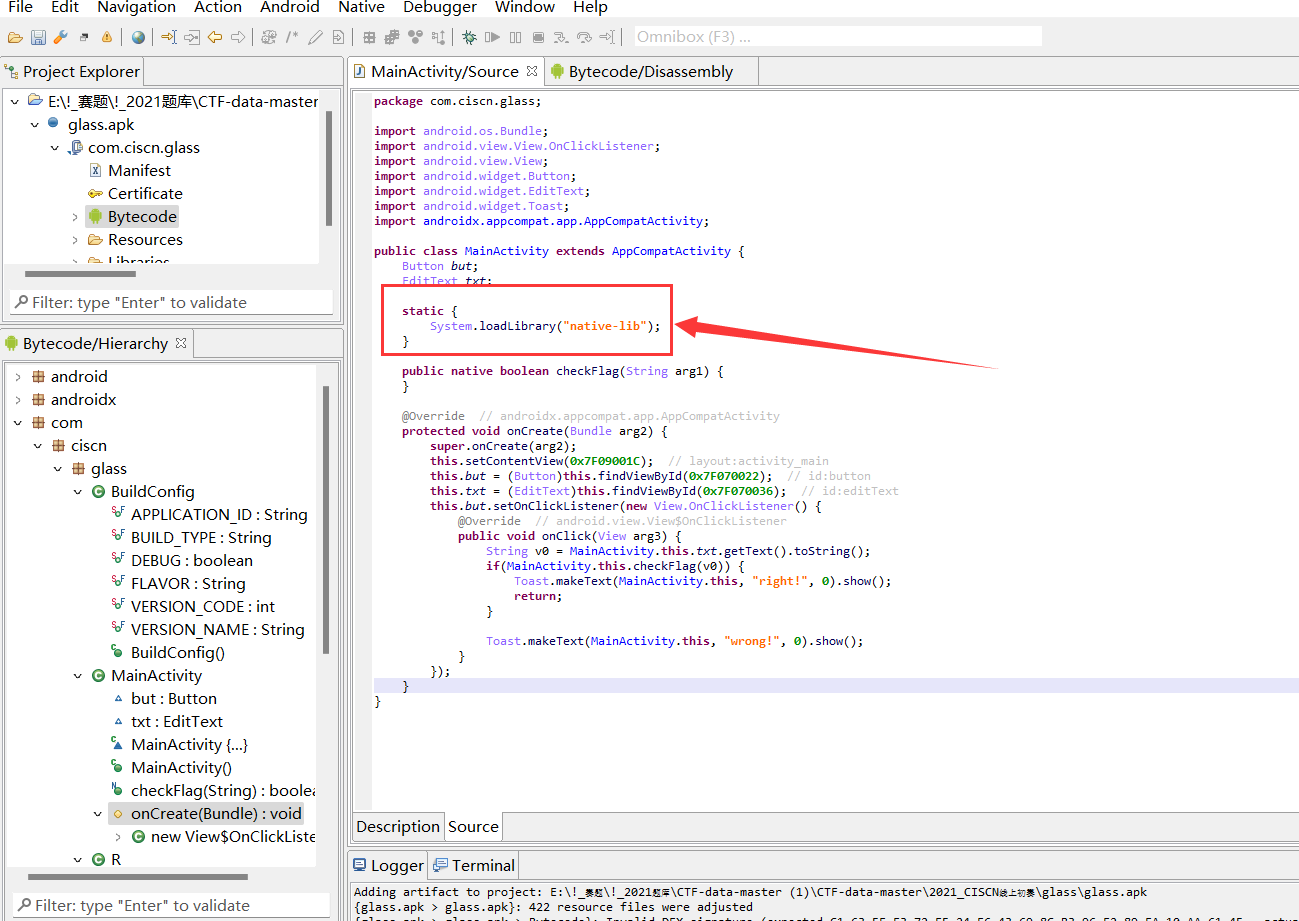
用jd-gui可以查看有一个so文件,
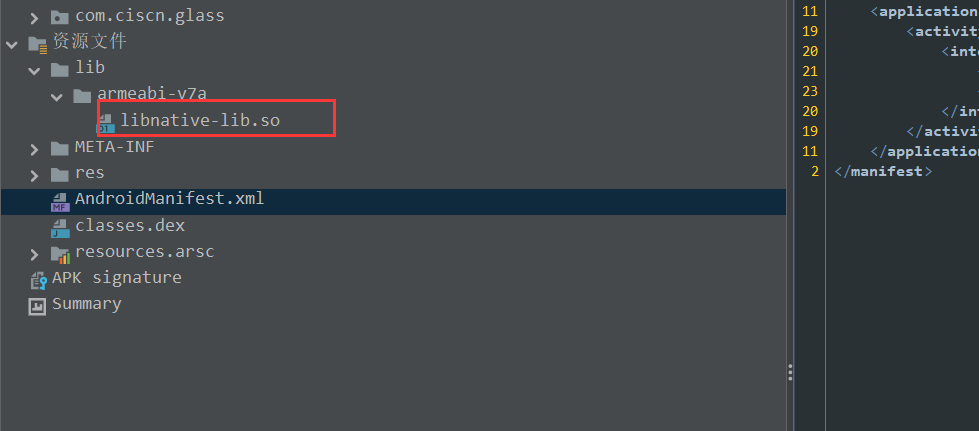
直接解压.apk文件,然后在lib-> armeabi-v7a -> 处找到.so文件,用ida32就能查看这个checkflag函数
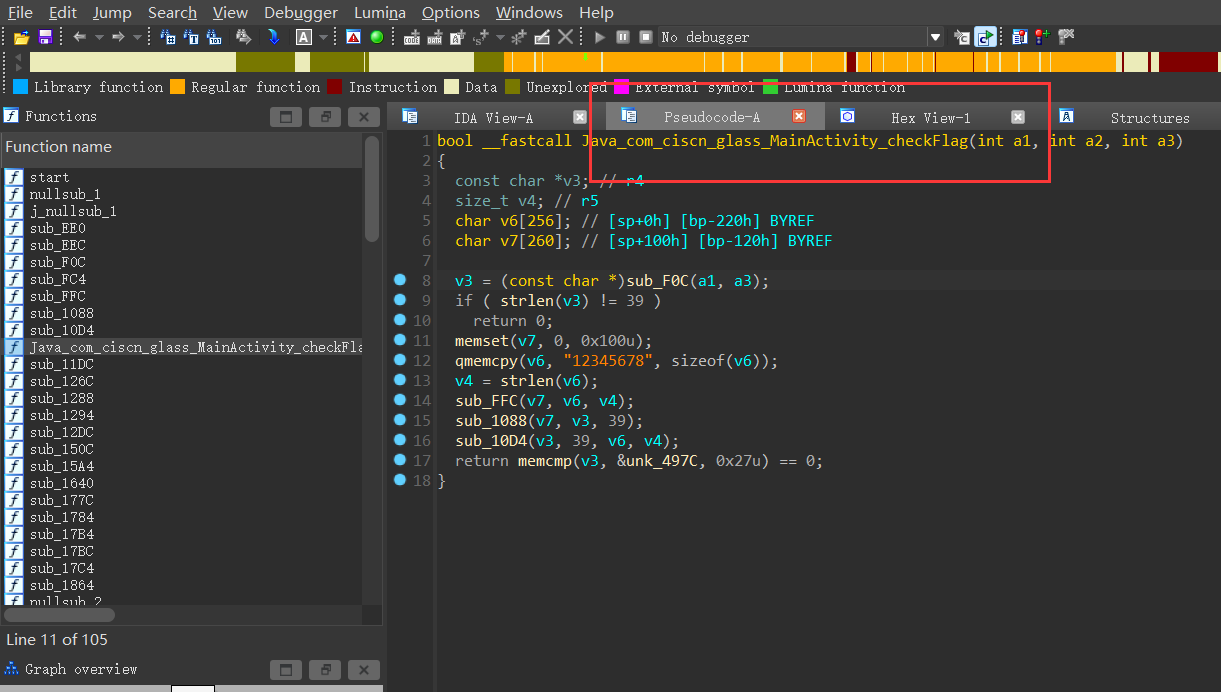
可以发现是RC4加密,可以查看我之前的一个博客,还有当时参考的大佬的一篇文章
sub_FFC函数是RC4加密的准备工作,数组S的置换以及生成密钥流


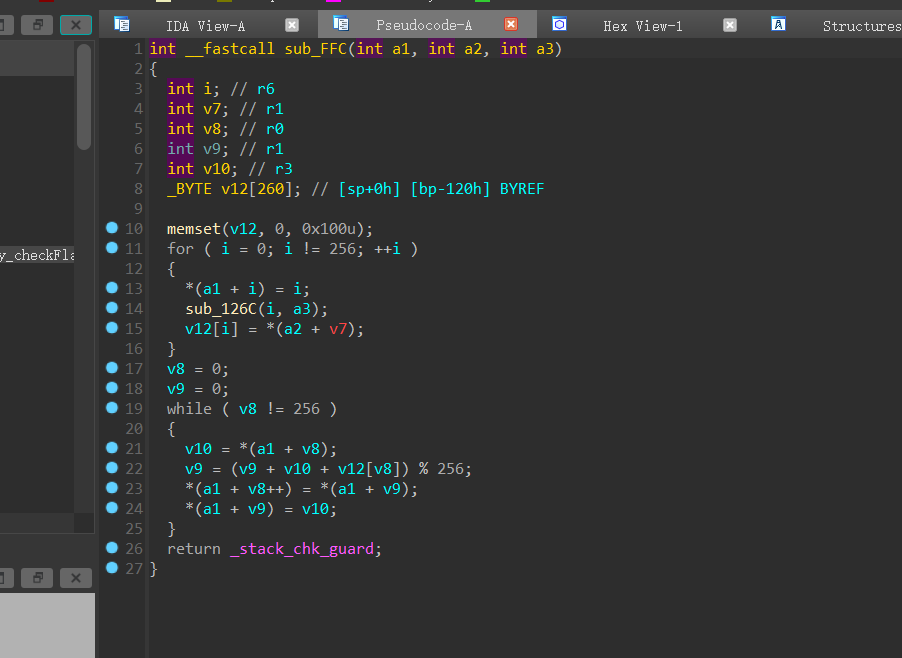
在经历了标准的RC4加密后,经过了第二个加密函数,39作为二参传入加密函数
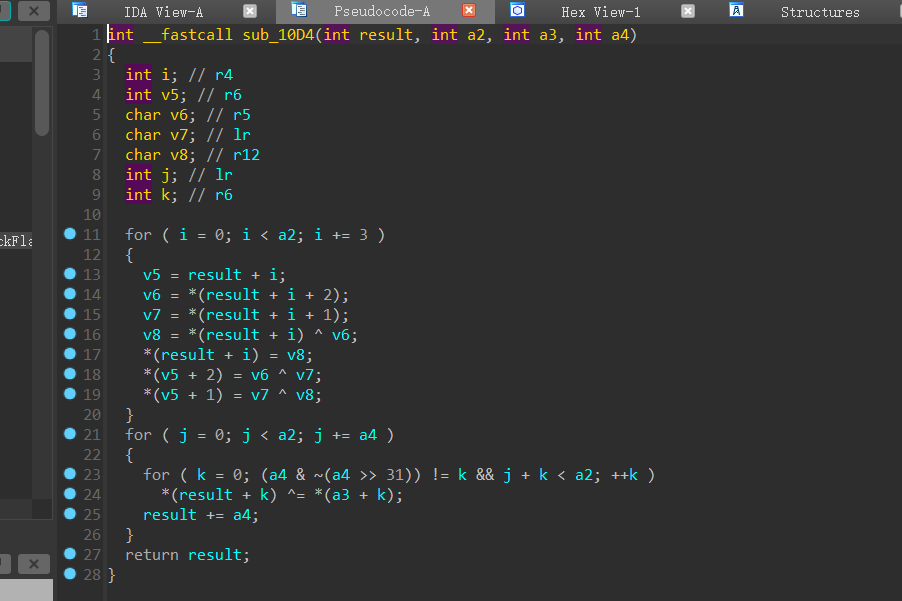
其中有两个for循环,第二个for循环根据xor的特性,照搬不动即可
第一个for循环,可以转换成以下的代码:
1 | data[i] = data[i] ^ data[i+2] |
最终结果是要与unk_497C数组做对比
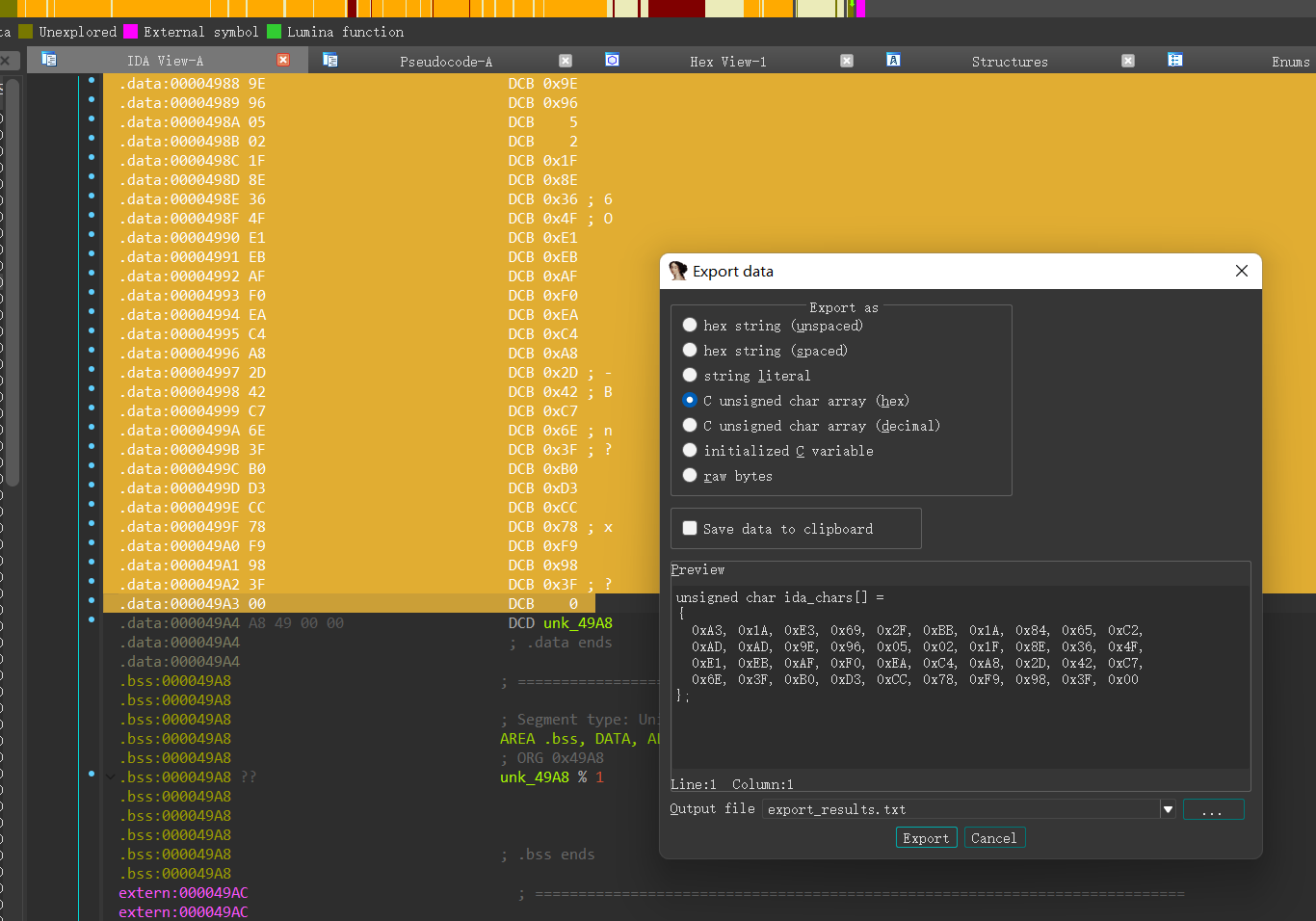
1 |
|
