2022 catf1agctf 部分WriteUp
Crypto
怎么会多一个呢
在线网站分解出来三个素数,和普通rsa解题一致
1 | import gmpy2 |
高实在是高
我看到题的时候发现e非常的小,就直接套低加密指数攻击那一套了
1 | from gmpy2 import iroot |
赛后看z1r0大师傅wp才发现是rsa中的已知明文m题型,看来rsa题还是得刷(orz)
用sage在线环境可以解出来
1 | import binascii |
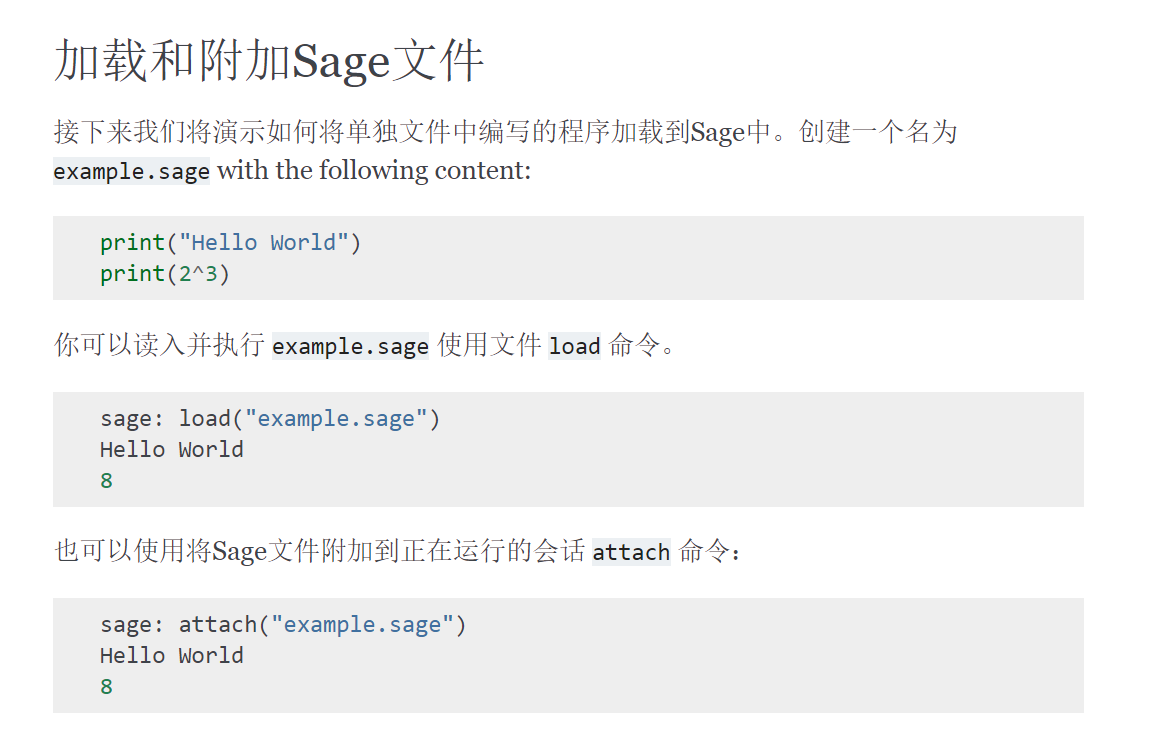
我这边就安装了一下sage环境,在github上下载完成后,双击安装包即可,可以多看看sage中文文档
sage的使用
load()和attach()两种方法皆可,attach()会根据sage文件的修改加载,比较推荐
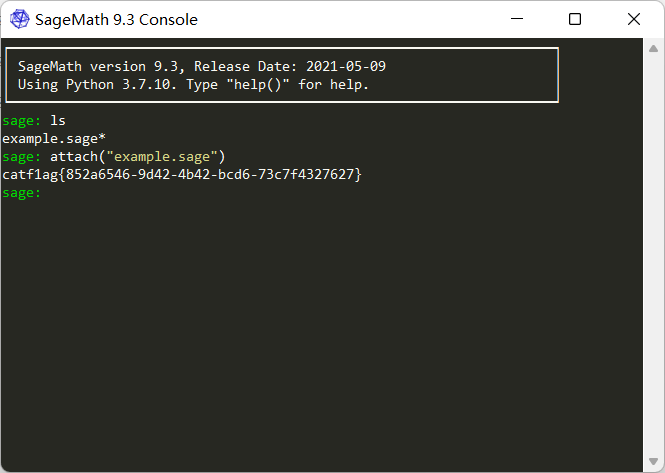
栓q
通过这篇博客可以知道短信息的内容部分使用的是unicode编码
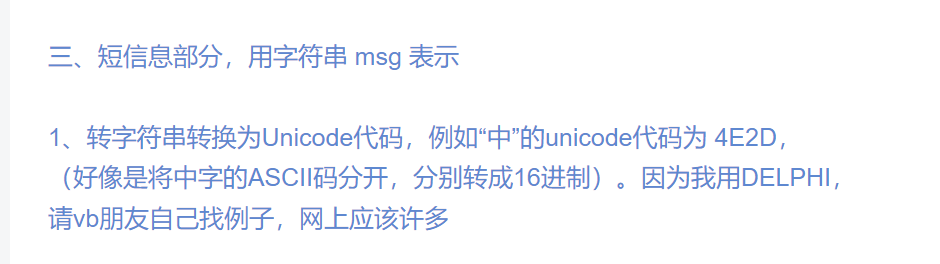
1 | string = [0x771F ,0x7684 ,0x662F ,0x6813 ,0x0051 ,0x7ED9 ,0x4F60 ,0x0066 ,0x006C ,0x0061,0x0067,0xFF1A,0x0063,0x0061,0x0074,0x0066,0x0031,0x0061,0x0067,0x007B,\ |
但是只发现了一半的flag
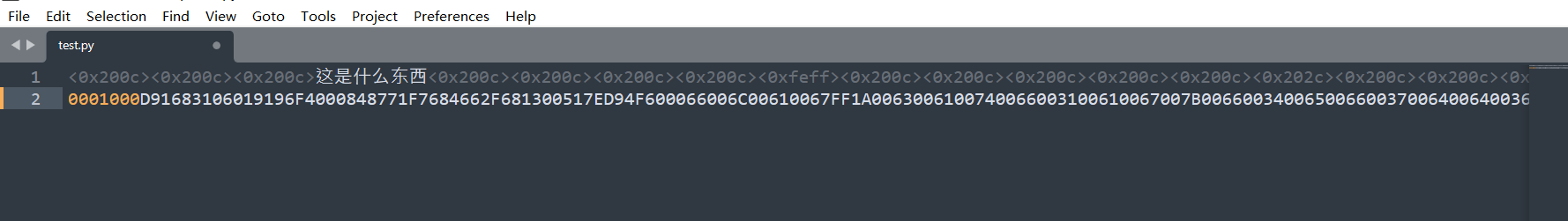
原来是零宽度字符隐写……放上大佬总结的文章
在线网站:http://330k.github.io/misc_tools/unicode_steganography.html
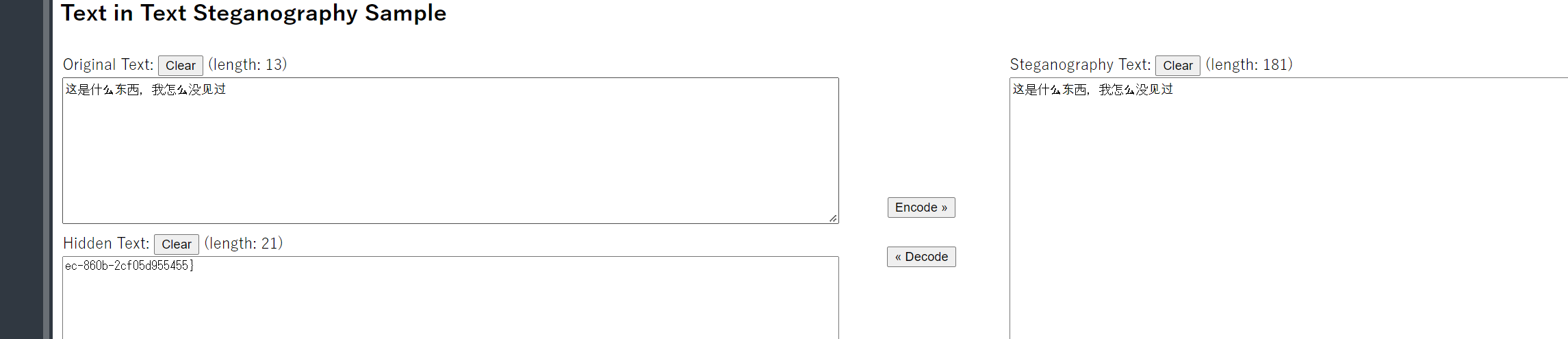
1 | # catf1ag{f4ef7dd6-cda1-11ec-860b-2cf05d95545} |
怕是我少见多怪了(orz)
