复现一下2022angstromctf
Crypto
[复现]Vinegar Factory
1 | #!/usr/local/bin/python3 |
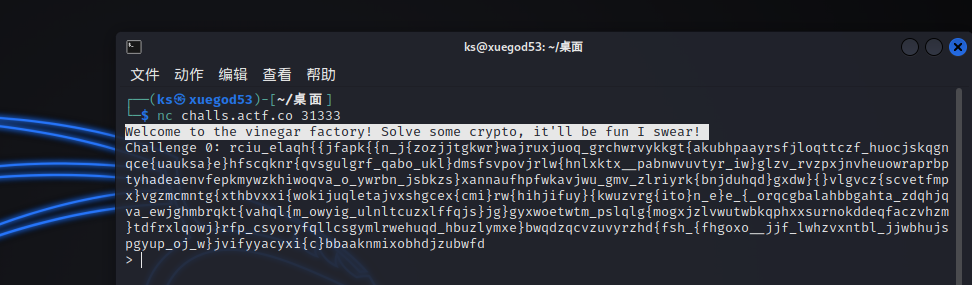
题目的意思是远端随机产生一个fleg,其被actf{}括起来,以及一个key,用key加密fleg+”fleg”字符串,并且将其仍到上千个字符中,并且服务端会在未输入的20秒之内关闭,在循环次数为50次的时候会将真正的flag放到noise字符串中。
1 | import string |
代码功能:
连接远端,提取noise字符串
粗略筛选匹配的字符串到文本文件中
在文本文件中,一行一行读取字符串,求出key,并且验证尾部的字符串是否是”fleg”,因为key一致
筛选完成后向服务端发送解密后的fleg
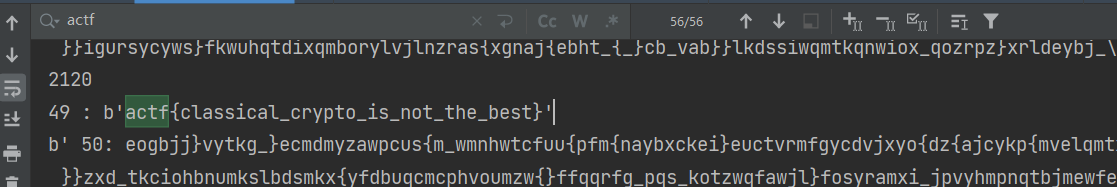
太强了,涉及到字符串的算法……
